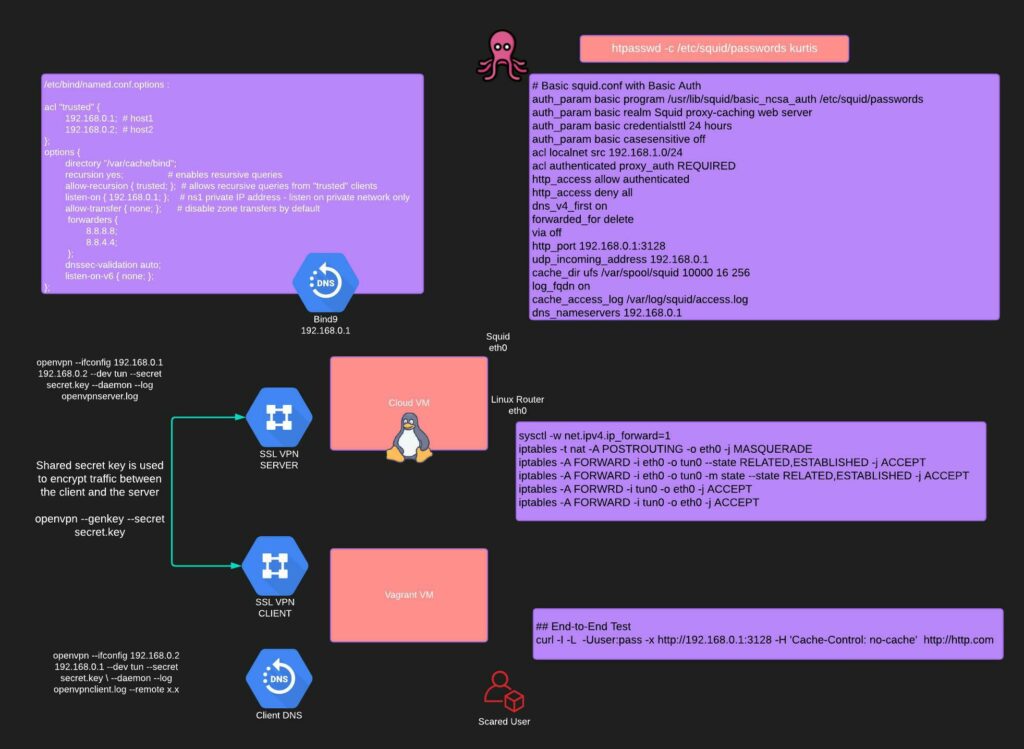
Workflow attempts to setup semi anonymous http(s)/dns proxy with openvpn symmetric key. Vagrant VM is the client and cloud VM is the server.
Example Vagrantfile
Vagrant.configure("2") do |config|
config.vm.box = "bento/ubuntu-20.04"
config.vm.network "forwarded_port", guest: 3000, host: 3000
config.vm.synced_folder "src/", "/host/code"
end
$ openssl enc -aes-256-cbc -in hi.txt -out hi.bin
enter aes-256-cbc encryption password:
Verifying - enter aes-256-cbc encryption password:
$ strings hi.bin
Salted__The private communication channel is implemented over a openvpn tunnel interface. Generate a symmetric private key and send it over the wire. Try openssl and ssh’ing it over:
Server config:
openvpn --genkey --secret secret.key
# Server side tunnel
openvpn --ifconfig 192.168.0.1 192.168.0.2 --dev tun --secret secret.key --daemon --log openvpnserver.log
# Client Side tunnel
openvpn --ifconfig 192.168.0.2 192.168.0.1 --dev tun --secret secret.key --daemon --log openvpnclient.log --remote my.cloud.ip
# into router with Masquerade for all Tun generated traffic
sysctl -w net.ipv4.ip_forward=1
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
iptables -A FORWARD -i eth0 -o tun0 --state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -i eth0 -o tun0 -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWRD -i tun0 -o eth0 -j ACCEPT
iptables -A FORWARD -i tun0 -o eth0 -j ACCEPT
# Server squid file
apt-get install apache2-utils squid
touch /etc/squid/passwords
chmod 777 /etc/squid/passwords
htpasswd -c /etc/squid/passwords kris
cat <EOF > /etc/squid.conf >
auth_param basic program /usr/lib/squid/basic_ncsa_auth /etc/squid/passwords
auth_param basic realm Squid proxy-caching web server
auth_param basic credentialsttl 24 hours
auth_param basic casesensitive off
acl authenticated proxy_auth REQUIRED
http_access allow authenticated
http_access deny all
dns_v4_first on
forwarded_for delete
via off
http_port 3128
EOF
##
# DNS forwarding proxy listening on tun0 interface only
##
cat <<EOF > /etc/bind/named.conf.options
acl "trusted" {
192.168.0.1; # host1
192.168.0.2; # host2
};
options {
directory "/var/cache/bind";
recursion yes; # enables resursive queries
allow-recursion { trusted; }; # allows recursive queries from "trusted" clients
listen-on { 192.168.0.1; }; # ns1 private IP address - listen on private network only
allow-transfer { none; }; # disable zone transfers by default
forwarders {
8.8.8.8;
8.8.4.4;
};
dnssec-validation auto;
listen-on-v6 { none; };
};
EOF
# Client test on server tail query logs to insure that dns request are being routed# Client Side tunnel
openvpn --ifconfig 192.168.0.2 192.168.0.1 --dev tun --secret secret.key --daemon --log openvpnclient.log --remote my.cloud.ip
curl -x http://192.168.0.1:3128 --dns-interface tun0 -Ykris:mypass --interface tun0 -H'Cache-Control: no-cache' http://ifconfig.me=
