Optimizing Container Workflows in DevOps: An Insight into SDLC and Runtime Management
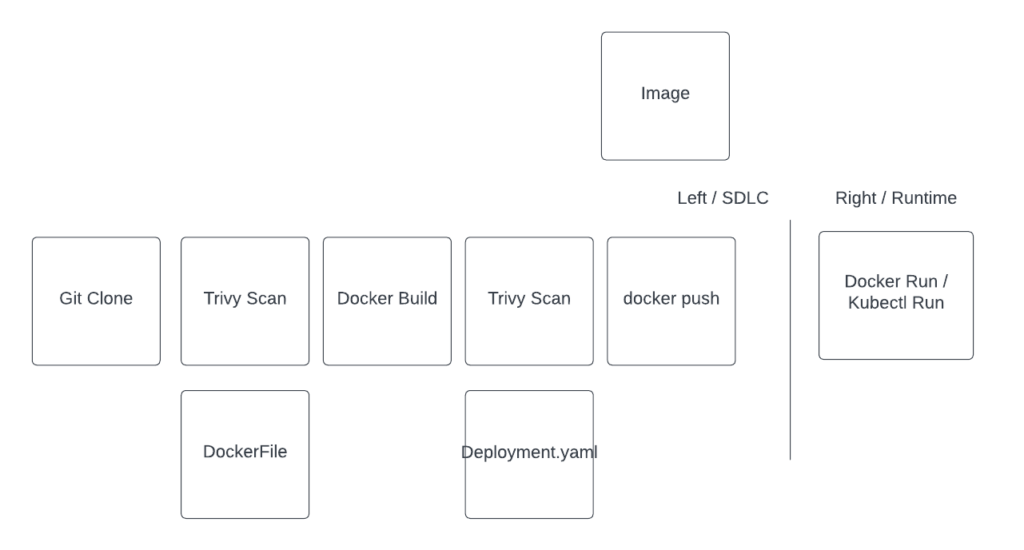
In today’s container-centric infrastructure landscape, DevOps professionals need a clear understanding of every tool and process involved. This article offers a concise overview, focusing on the culmination of the Software Development Life Cycle (SDLC) with container image deployment and subsequent monitoring.
Let’s begin with a high-level workflow representation:
- Source Code Management: At the heart of every DevOps pipeline is a version control system.
Gitstands out as the de facto standard, providing a robust platform for hosting repositories, collaborating on code, and initiating CI/CD processes. - Security Scanning:
Trivyis an exemplary tool for static Common Vulnerabilities and Exposures (CVE) analysis. This step ensures that the container images are devoid of known security vulnerabilities before they reach the production environment. - Containerization: With security checks in place, we move to the container building phase.
Dockercommand
Transitioning to the runtime phase:xz
- Runtime: This represents the live environment where the application container is up and running. Managing runtime efficiently is pivotal for application health and performance.
- Monitoring & Security: In dynamic environments, passive monitoring isn’t enough. Active agents are required to both monitor and safeguard running workloads. were’re spotlighting the
Aqua eBPF Traceeapplication in this context. eBPF (Extended Berkeley Packet Filter) is a revolutionary technology enabling superior observability, and when coupled with Aqua’s tracee, it provides an unparalleled runtime monitoring solution.
Table of Contents
Shift Left SDLC
“Shift Left” in DevOps:
“shifting left” So, what’s it all about?
- Handling Dependencies: First up, we’ve got to pull in our dependencies.
- The Magic of Containerization: Once our code’s all prepped, we package it up using a
Dockerfile. A container image, ready to be deployed and turned into a running workload
the fun doesn’t stop there:
- Looking for Code Gremlins: Before letting our code out into the wild, we’ve got to check for any sneaky vulnerabilities
- IaC Shenanigans: Ever use Terraform or something similar? It’s fantastic, but sometimes, things can go sideway. Imagine accidentally making your RDS database public.
- Kubernetes Tune-up: If you’re playing in the Kubernetes world, you know how easy it is to misconfigure stuff. Like forgetting to set limits, authorized Ingress host names, PSP
- Dockerfile Double-Check: And of course, we have to make sure our Dockerfile is using secure best practices. Running processes as the root user? That’s a no-no.
In a nutshell, “shifting left” is all about catching issues early. This is DevOps adventure, keeping things tight, right, and secure from the get-go.
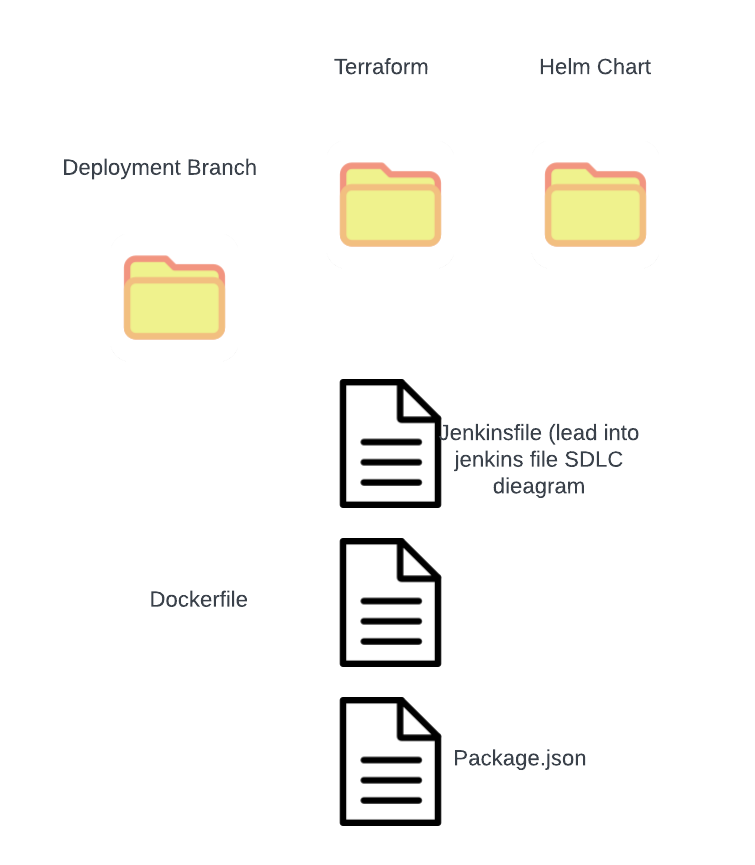
Inside the Git Repo Universe
Your git repo? It’s not just about app code.
- Got a
Dockerfile? That’s our container Image recipe. - Spotted a
Jenkinsfile? That’s the backstage magic and facilitates all build steps composing your SDLC. - Terraform files, Kubernetes YAMLs, or Helm charts? Our infrastructure deployment code.
In short, a git repo isn’t just storage—it’s an ecosystem.
Jenkinsfile
- Break down process into stages
- Defined in version control
- Utilizes gates that assess different parts of the build
pipeline {
agent any
environment {
APP = 'headers'
VERSION = "0.0.1"
GIT_HASH = """${sh(
returnStdout: true,
script: 'git rev-parse --short HEAD'
)}"""
dockerhub=credentials('dockerhub')
}
stages {
stage('Remote Code Repo Scan') {
steps {
echo "Running ${env.BUILD_ID} on ${env.JENKINS_URL}"
sh "trivy repo --exit-code 192 https://github.com/kurtiepie/headers.git"
}
}
stage('Code Base Scan') {
steps {
sh "trivy fs --exit-code 192 --severity HIGH,CRITICAL --skip-dirs ssl ."
}
}
stage('Docker Build') {
steps {
sh "docker build . -t ${APP}:${VERSION}-${GIT_HASH}"
}
}
stage('Scan Generated Image Docker') {
steps {
sh "trivy image ${APP}:${VERSION}-${GIT_HASH}"
}
}
stage('Push Docker Image to docker hub') {
steps {
sh 'echo docker tag ${APP}:${VERSION}-${GIT_HASH} kvad/headers:0.0.2'
sh 'echo $dockerhub_PSW | docker login -u $dockerhub_USR --password-stdin'
sh 'docker push kvad/headers:0.0.2'
}
}
stage('Scan Helm IAC FILES') {
steps {
sh "helm template headerschart/ > temp.yaml"
sh "trivy --severity HIGH,CRITICAL --exit-code 192 config ./temp.yaml"
sh "rm ./temp.yaml"
}
}
}
}Dockerfile
FROM golang:1.16-alpine as builder
WORKDIR /app
COPY go.mod ./
COPY go.sum ./
RUN go mod download
COPY *.go ./
RUN go build -o ./headers
from alpine
COPY --from=builder /app/headers /bin/headers
# No root user
RUN adduser -D headeruser && chown headeruser /bin/headers
USER root
CMD [ "/bin/headers"]Insure secure best practices are being followed
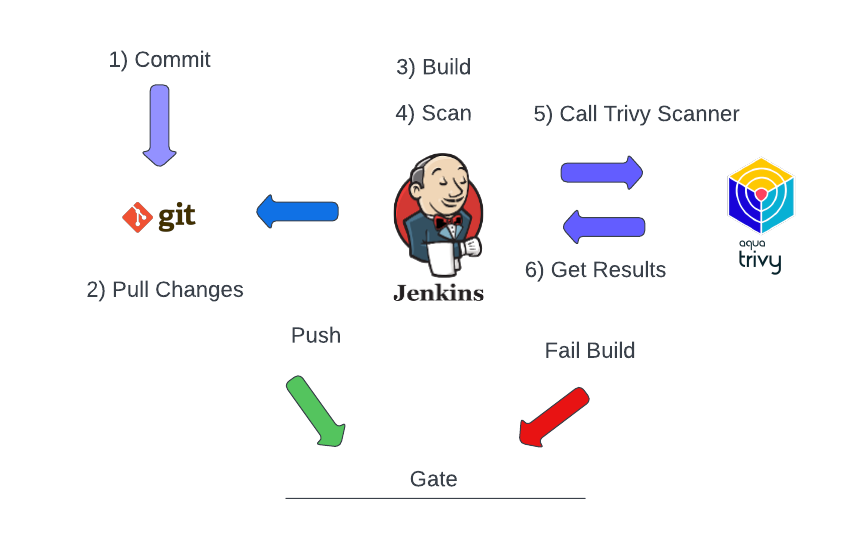
Using Trivy in this case? It’s to spot any nasty high-severity CVEs in our image.
Right side / Runtime
For applications, runtime is the endgame. Amidst diverse runtime workloads, many deploy without update capabilities. Ensure security with agents for behavioral monitoring, malware scans, and attack prevention.
